300-415: Implementing Cisco SD-WAN Solutions (ENSDWI) Part 2
Question #: 51
Topic #: 1
Refer to the exhibit. vManage and vBond have an issue establishing a connection with each other. Which action resolves the issue?
A. Change the organization name on both controllers to match viptela.com.
B. Configure the encapsulation ipsec command under the tunnel interface on vManage.
C. Reconfigure the system IPs to belong to the same subnet.
D. Remove the encapsulation ipsec command under the tunnel interface of vBond.
Selected Answer: A
Question #: 52
Topic #: 1
Refer to the exhibit. An engineer is getting a CTORGNMMIS error on a controller connection. Which action resolves this issue?
A. Configure a valid certificate on vSMART.
B. Configure a valid organization name.
C. Configure a valid serial number on the WAN Edge.
D. Configure a valid product ID.
Selected Answer: B
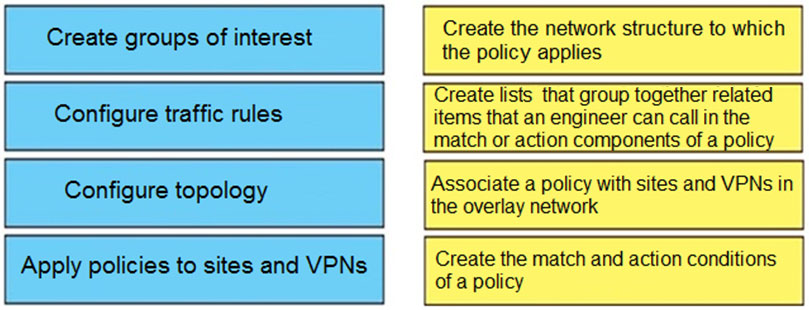
Question #: 53
Topic #: 1
DRAG DROP –
Drag and drop the vManage policy configuration procedures from the left onto the correct definitions on the right.
Select and Place:
Suggestion Answer:
Question #: 54
Topic #: 1
A vEdge platform is sending VRRP advertisement messages every 10 seconds. Which value configures the router back to the default timer?
A. 2 seconds
B. 5 seconds
C. 1 second
D. 3 seconds
Selected Answer: C
Question #: 55
Topic #: 1
Which two services are critical for zero touch provisioning on-boarding? (Choose two.)
A. EMAIL
B. SNMP
C. AAA
D. DHCP
E. DNS
Selected Answer: D
Question #: 56
Topic #: 1
When redistribution is configured between OMP and BGP at two Data Center sites (DC) that have Direct Connection Interlink, which step avoids learning the same routes on WAN Edge routers of the DCs from LAN?
A. Set down-bit on WAN Edge routers on DC1
B. Define different VRFs on both DCs
C. Set OMP admin distance lower than BGP admin distance
D. Set same overlay AS on both DC WAN Edge routers
Selected Answer: D
Question #: 57
Topic #: 1
Which device information is required on PNP/ZTP to support the zero touch onboarding process?
A. serial and chassis numbers
B. interface IP address
C. public DNS entry
D. system IP address
Selected Answer: A
Question #: 58
Topic #: 1
Which configuration step is taken on vManage after WAN Edge list is uploaded to support the on-boarding process before the device comes online?
A. Verify the device certificate
B. Enable the ZTP process
C. Set the device as valid
D. Send the list to controllers
Selected Answer: C
Question #: 59
Topic #: 1
On which device is a service FW address configured to insert firewall service at the hub?
A. vSmart at the branch
B. vEdge at the branch
C. vEdge at the hub
D. vSmart at the hub
Selected Answer: C
Question #: 60
Topic #: 1
Which attributes are configured to uniquely identify and represent a TLOC route?
A. system IP address, link color, and encapsulation
B. origin, originator, and preference
C. site ID, tag, and VPN
D. firewall, IPS, and application optimization
Selected Answer: D
Question #: 61
Topic #: 1
Which type of route advertisement of OMP can be verified?
A. Origin, TLOC, and VPN
B. Origin, TLOC, and service
C. OMP, VPN, and origin
D. OMP, TLOC, and service
Selected Answer: D
Question #: 62
Topic #: 1
Which command displays BFD session summary information per TLOC on vEdge routers?
A. show bfd tloc-summary-list
B. show bfd history
C. show bfd summary
D. show bfd sessions
Selected Answer: D
Question #: 63
Topic #: 1
Two sites have one WAN Edge each. Each WAN Edge has two public TLOCs with no restrict configured. There is full reachability between the TLOCs. How many data tunnels are formed on each WAN Edge router?
A. 6
B. 2
C. 4
D. 8
Selected Answer: C
Question #: 64
Topic #: 1
Which command on a WAN Edge device displays the information about the colors present in the fabric that are learned from vSmart via OMP?
A. show omp peers
B. show omp route
C. show omp sessions
D. show omp tlocs
Selected Answer: D
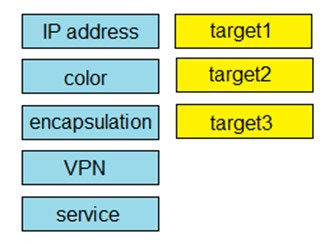
Question #: 65
Topic #: 1
DRAG DROP –
Drag and drop the attributes from the left that make each transport location unique onto the right. Not all options are used.
Select and Place:
Suggestion Answer:
Question #: 66
Topic #: 1
Which two WAN Edge devices should be deployed in a cloud? (Choose two.)
A. ASR1000v
B. vEdge 100wm
C. CSR1000v
D. vEdge cloud
E. vEdge 5000v
Selected Answer: CD
Question #: 67
Topic #: 1
Refer to the exhibit. Which binding is created using the tloc-extension command?
A. between ge 0/2.101 of port-type transport and ge 0/0 of port-type service
B. between ge 0/2.101 of port-type service and ge 0/0 of port-type service
C. between ge 0/2.101 of port-type service and ge 0/0 of port-type transport
D. between ge 0/2.101 of port-type transport and ge 0/0 of port-type transport
Selected Answer: D
Question #: 68
Topic #: 1
Which feature builds transport redundancy by using the cross link between two redundant WAN Edge routers?
A. TLOC extension
B. quality of service
C. zero-touch provisioning
D. OMP
Selected Answer: A
Question #: 69
Topic #: 1
In a Cisco SD-WAN architecture, what is the role of the WAN Edge?
A. It provides orchestration to assist automatic provisioning of WAN Edge routers and overlay
B. It is the management plane responsible for centralized configuration and monitoring
C. It is the control plane that builds and maintains network topology
D. It is the data plane that is responsible for forwarding traffic
Selected Answer: D
Question #: 70
Topic #: 1
Which TCP Optimization feature is used by WAN Edge to prevent unnecessary retransmissions and large initial TCP window sizes to maximize throughput and achieve a better quality?
A. SACK
B. SEQ
C. RTT
D. SYN
Selected Answer: A
Question #: 71
Topic #: 1
A network administrator is configuring VRRP to avoid a traffic black hole when the transport side of the network is down on the primary device. What must be configured to get the fastest failover to standby?
A. OMP tracking
B. higher group ID number
C. prefix-list tracking
D. lower timer interval
Selected Answer: C
Question #: 72
Topic #: 1
Which policy blocks TLOCs from remotes and allows TLOCs from the data center to form hub-and-spoke peering?
A. centralized data policy
B. localized control policy
C. centralized control policy
D. localized data policy
Selected Answer: C
Question #: 73
Topic #: 1
Which plane assists in the automatic onboarding of the SD-WAN routers into the SD-WAN overlay?
A. data
B. orchestration
C. management
D. control
Selected Answer: B
Question #: 74
Topic #: 1
Which component is responsible for routing protocols such as BGP and OSPF in a Cisco SD-WAN solution?
A. vSmart Controller
B. WAN Edge Router
C. vManage
D. vBond Orchestrator
Selected Answer: A
Question #: 75
Topic #: 1
What are the two protocols redistributed into OMP? (Choose two.)
A. OSPF
B. RSVP
C. LDP
D. RIP
E. EIGRP
Selected Answer: AE
Question #: 76
Topic #: 1
How does the replicator role function in Cisco SD-WAN?
A. WAN Edge devices advertise the rendezvous point to all the receivers through the overlay network.
B. WAN Edge devices advertise the rendezvous point to all the receivers through the underlay network.
C. vSmart Controllers advertise the rendezvous point to all the receivers through the overlay network.
D. vSmart Controllers advertise the rendezvous point to all the receivers through the underlay network.
Selected Answer: C
Question #: 77
Topic #: 1
Refer to the exhibit. Which configuration extends the INET interface on R1 to be used by R2 for control and data connections?
A. R1 interface ge0/2 interface ge0/2.10 ip address 43.43.43.2/30 tloc-extension ge0/0 tunnel-interface color public-internet R2 interface ge0/2 interface ge0/2.10 ip address 43.43.43.1/30 tunnel-interface color public-internet
B. R1 interface ge0/2 mtu 1504 no shutdown interface ge0/2.10 ip address 43.43.43.2/30 tunnel-interface color public-internet R2 interface ge0/2 mtu 1504 no shutdown interface ge0/2.10 ip address 43.43.43.1/30 tloc-extension ge0/0
C. R1 interface ge0/2 mtu 1504 no shutdown interface ge0/2.10 ip address 43.43.43.2/30 tloc-extension ge0/0 R2 interface ge0/2 mtu 1504 no shutdown interface ge0/2.10 ip address 43.43.43.1/30 tunnel-interface color public-internet
D. R1 interface ge0/2 no shutdown interface ge0/2.10 ip address 43.43.43.2/30 tloc-extension ge0/0 R2 interface ge0/2 no shutdown interface ge0/2.10 ip address 43.43.43.1/30 tloc-extension ge0/0
Selected Answer: C
Question #: 78
Topic #: 1
Refer to the exhibit. Which configuration value is used to change the administrative distance of iBGP routes to 20?
A. Configure Internal Routes Distance to 20.
B. Configure Propagate AS Path to off.
C. Configure Local Routes Distance to 20.
D. Configure External Routes Distance to 20.
Selected Answer: A
Question #: 79
Topic #: 1
How is multicast routing enabled on devices in the Cisco SD-WAN overlay network?
A. The WAN Edge routers originate multicast service routes to the vSmart controller via OMP, which then forwards joins for requested multicast groups based on IGMP v2 or v3 toward the source or PIM-RP as specified in the original PIM join message.
B. The WAN Edge routers originate multicast service routes to the vSmart controller via OMP, which then forwards joins for requested multicast groups based on IGMP v1 or v2 toward the source or PIM-RP as specified in the original PIM join message.
C. The vSmart controller originates multicast service routes to the WAN Edge routers via OMP, which then forwards joins for requested multicast groups based on IGMP v1 or v2 toward the source or PIM-RP as specified in the original PIM join message.
D. The vSmart controller originates multicast service routes to the WAN Edge routers via OMP, which then forwards joins for requested multicast groups based on IGMP v2 or v3 toward the source or PIM-RP as specified in the original PIM join message.
Selected Answer: B
Question #: 80
Topic #: 1
WAN Edge routers are configured manually to use UDP port offset to use nondefault offset values when IPsec tunnels are created. What is the offset range?
A. 1-19
B. 0-18
C. 0-19
D. 1-18
Selected Answer: C
Question #: 81
Topic #: 1
In which VPN is the NAT operation on an outgoing interface configured for direct Internet access?
A. 0
B. 512
C. 10
D. 1
Selected Answer: A
Question #: 82
Topic #: 1
Which SD-WAN component is configured to enforce a policy to redirect branch-to-branch traffic toward a network service such as a firewall or IPS?
A. vBond
B. vSmart
C. WAN Edge
D. Firewall
Selected Answer: C
Question #: 83
Topic #: 1
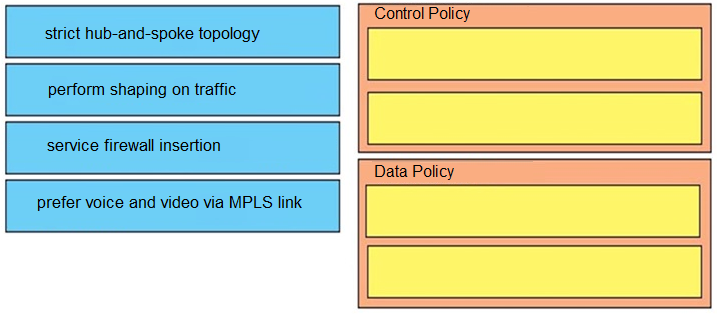
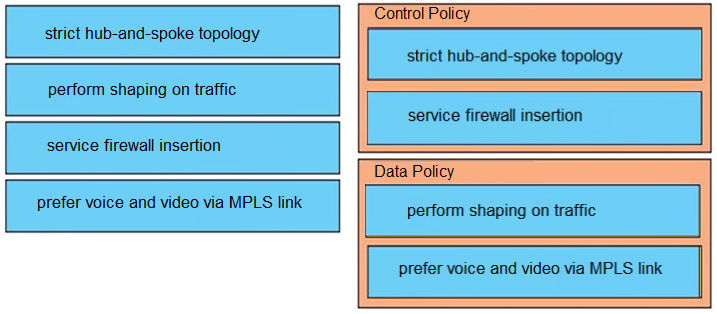
DRAG DROP –
Drag and drop the policies from the left onto the policy types on the right.
Select and Place:
Suggestion Answer:
Question #: 84
Topic #: 1
Which command verifies a policy that has been pushed to the vEdge router?
A. vSmart# show running-config policy
B. vEdge# show running-config data policy
C. vSmart# show running-config apply policy
D. vEdge# show policy from-vsmart
Selected Answer: D
Question #: 85
Topic #: 1
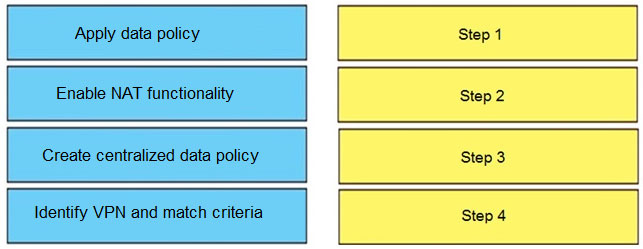
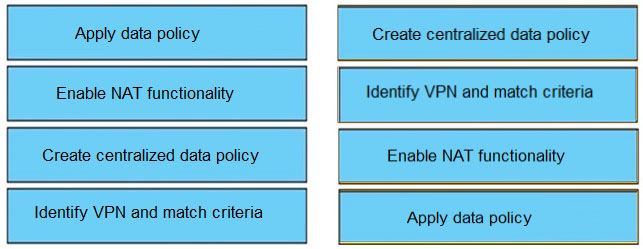
DRAG DROP –
Drag and drop the actions from the left into the correct sequence on the right to create a data policy to direct traffic to the Internet exit.
Select and Place:
Suggestion Answer:
Question #: 86
Topic #: 1
Which policy configures an application-aware routing policy under Configuration > Policies?
A. Data policy
B. Centralized policy
C. Localized policy
D. Control policy
Selected Answer: B
Question #: 87
Topic #: 1
Which policy is configured to ensure that a voice packet is always sent on the link with less than a 50 msec delay?
A. localized data policy
B. centralized control policy
C. localized control policy
D. centralized data policy
Selected Answer: A
Question #: 88
Topic #: 1
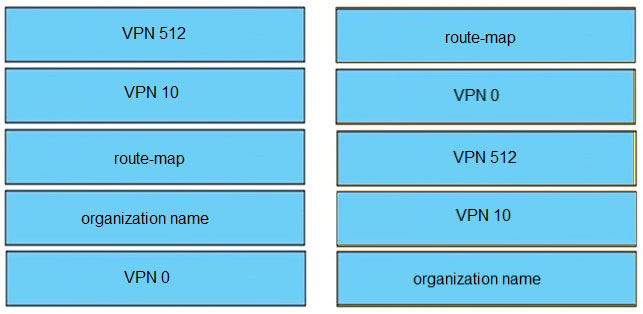
DRAG DROP –
Drag and drop the functions from the left onto the correct templates on the right.
Select and Place:
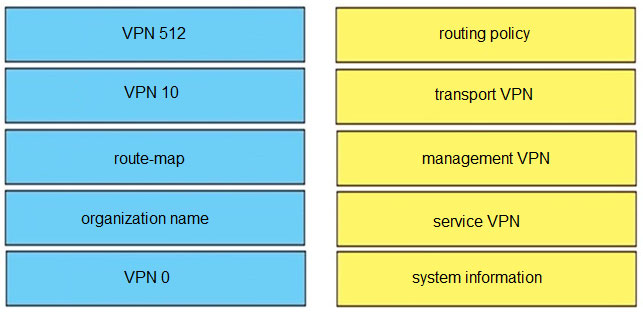
Suggestion Answer:
Question #: 89
Topic #: 1
When VPNs are grouped to create destination zone in Zone-Based Firewall, how many zones can a single VPN be part of?
A. two
B. four
C. one
D. three
Selected Answer: C
Question #: 90
Topic #: 1
An engineer wants to track tunnel characteristics within a SLA-based policy for convergence. Which policy configuration will achieve this goal?
A. app-route policy
B. VPN membership policy
C. control policy
D. data policy
Selected Answer: A
Question #: 91
Topic #: 1
An administrator needs to configure Cisco SD-WAN to divert traffic from the company’s private network to an ISP network. Which action should be taken to accomplish this goal?
A. configure the security policy
B. configure the control policy
C. configure the data policy
D. configure the application aware policy
Selected Answer: B
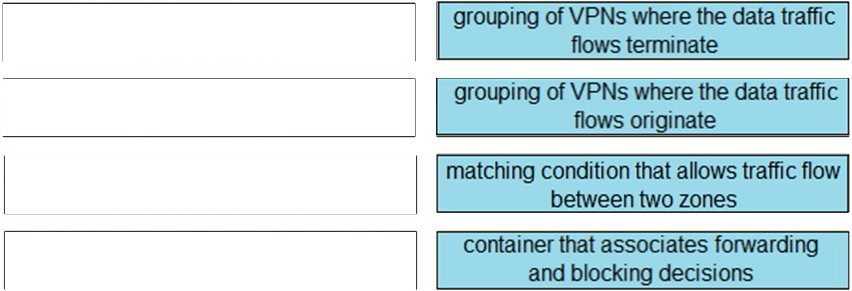
Question #: 92
Topic #: 1
DRAG DROP –
Drag and drop the definitions from the left to the configuration on the right.
Select and Place:
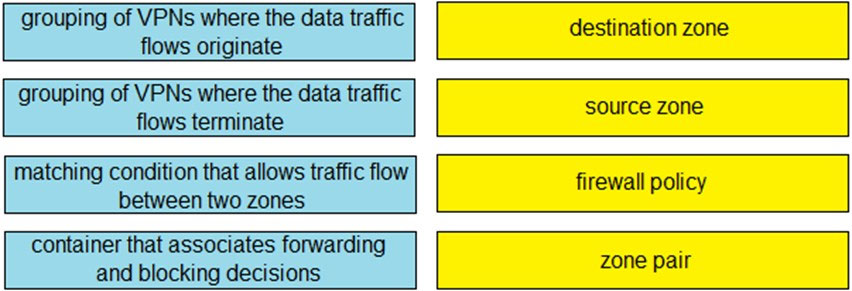
Suggestion Answer:
Question #: 93
Topic #: 1
An engineer is configuring a centralized policy to influence network route advertisement. Which controller delivers this policy to the fabric?
A. vSmart
B. vBond
C. vManage
D. WAN Edge
Selected Answer: A
Question #: 94
Topic #: 1
Which VPN connects the transport-side WAN Edge interface to the underlay/WAN network?
A. VPN 1
B. VPN 0
C. VPN 512
D. VPN 511
Selected Answer: C
Question #: 95
Topic #: 1
An engineer is configuring a list that matches all IP prefixes with lengths from /1 to /16 in a centralized control policy. Which list accomplishes this task?
A. 0.0.0.0/0 le 16
B. 0.0.0.0/1 le 16
C. 0.0.0.0/0 ge 1
D. 0.0.0.0/16 ge 1
Selected Answer: B
Question #: 96
Topic #: 1
An engineer is configuring a data policy for packets that must be captured through the policy. Which command accomplishes this task?
A. policy > data-policy > vpn-list > sequence > default-action > accept
B. policy > data-policy > vpn-list > sequence > match
C. policy > data-policy > vpn-list > sequence > action
D. policy > data-policy > vpn-list > sequence > default-action > drop
Selected Answer: B
Question #: 97
Topic #: 1
An administrator must configure an ACL for traffic coming in from the service-side VPN on a specific WAN Edge device with circuit ID 123456789. Which policy must be used to configure this ACL?
A. local data policy
B. central data policy
C. app-aware policy
D. central control policy
Selected Answer: A
Question #: 98
Topic #: 1
Refer to the exhibit. An administrator is configuring a policy in addition to an existing hub-and-spoke policy for two sites that should directly communicate with each other. How is this policy configured?
A. mesh
B. custom control (route and TLOC)
C. hub-and-spoke
D. import existing topology
Selected Answer: B
Question #: 99
Topic #: 1
Which feature allows reachability to an organization’s internally hosted applications for an active DNS security policy on a device?
A. data policy with redirect
B. local domain bypass
C. DNSCrypt configuration
D. DHCP option 6
Selected Answer: B
Question #: 100
Topic #: 1
A network administrator is configuring a centralized control policy based on match action pairs for multiple conditions. Which order must be configured to prefer
Prefix List over TLOC and TLOC over Origin?
A. deterministic order
B. lowest to highest sequence number
C. highest to lowest sequence number
D. nonsequential order
Selected Answer: B

