300-420: Designing Cisco Enterprise Networks (ENSLD) Part 2
Question #: 51
Topic #: 1
When vEdge router redundancy is designed, which FHRP is supported?
A. HSRP
B. OMP
C. GLBP
D. VRRP
Selected Answer: D
Question #: 52
Topic #: 1
What is the purpose of an edge node in an SD-Access network fabric?
A. Edge nodes identify and authenticate endpoints and register endpoint information with control plane nodes.
B. Edge nodes track endpoint IDs to location mappings, along with IPv4, IPv6, or MAC addresses.
C. Edge nodes are the gateway between the fabric domain and network outside of the fabric.
D. Edge nodes resolve lookup requests from edge and border nodes to locate destination endpoint IDs.
Selected Answer: A
Question #: 53
Topic #: 1
Which component of Cisco SD-Access integrates with Cisco DNA Center to perform policy segmentation and enforcement through the use of security group access control lists and security group tags?
A. Cisco Application Policy Infrastructure Controller Enterprise Module
B. Cisco Network Data Platform
C. Cisco Identity Services Engine
D. Cisco TrustSec
Selected Answer: C
Question #: 54
Topic #: 1
Which design element should an engineer consider when multicast is included in a Cisco SD-Access architecture?
A. PIM SSM must run in the underlay.
B. Multicast clients reside in the underlay, and the multicast source is outside the fabric or in the overlay.
C. Rendezvous points must be used in a PIM SSM deployment.
D. Multicast traffic is transported in the overlay and the EID space for wired and wireless clients.
Selected Answer: A
Question #: 55
Topic #: 1
What is the role of a control-plane node in a Cisco SD-Access architecture?
A. fabric device that connects wired endpoints to the SD-Access fabric
B. map system that manages endpoint to device relationships
C. fabric device that connects APs and wireless endpoints to the SD-Access fabric
D. map system that manages External Layer 3 networks
Selected Answer: B
Question #: 56
Topic #: 1
How is end-to-end microsegmentation enforced in a Cisco SD-Access architecture?
A. VLANs are used to segment traffic at Layer 2.
B. 5-tuples and ACLs are used to permit or deny traffic.
C. SGTs and SGTACLs are used to control access to various resources.
D. VRFs are used to segment traffic at Layer 3.
Selected Answer: C
Question #: 57
Topic #: 1
Which two border nodes are available in the Cisco SD-Access architecture? (Choose two.)
A. extended border
B. edge border
C. internal border
D. anywhere border
E. intermediate border
Selected Answer: CD
Question #: 58
Topic #: 1
Which control-plane protocol is used to map an endpoint to a location in a Cisco SD-Access network?
A. FabricPath
B. IS-IS
C. LISP
D. MP-BGP
Selected Answer: C
Question #: 59
Topic #: 1
Which feature is required for graceful restart to recover from a processor failure?
A. Cisco Express Forwarding
B. Virtual Switch System
C. Stateful Switchover
D. Bidirectional Forwarding Detection
Selected Answer: C
Question #: 60
Topic #: 1
An architect is designing a network that will utilize the spanning tree protocol to ensure a loop-free topology. The network will support an engineering environment where it is necessary for end-users to connect their own network switches for testing purposes. Which feature should the architect include in the design to ensure the spanning-tree topology is not affected by these rogue switches?
A. BPDU Skew Detection
B. BPDU guard
C. loop guard
D. root guard
Selected Answer: D
Question #: 61
Topic #: 1
An engineer is designing a Layer 3 campus network running EIGRP between the core, aggregation, and access layers. The access layer switches will be connected to the aggregation layer using Layer 3 copper connections. The engineer wants to improve the convergence time for access layer switch failures.
Which technique must the design include?
A. enabling BFD for EIGRP on the access layer uplinks
B. reducing the EIGRP Hello / Hold timer values
C. EIGRP summarization from core to aggregation layer
D. EIGRP summarization from access to aggregation layer
Selected Answer: A
Question #: 62
Topic #: 1
An existing network solution is using BFD in echo mode. Several network devices are experiencing high CPU utilization, which an engineer has determined is related to the BFD feature. Which solution should the engineer leverage to reduce the CPU load?
A. Implement slow timers between peers with low CPU resources.
B. Implement BFD asynchronous mode between peers with low CPU resources.
C. Enable BFD multi-hop on the devices with low CPU resources.
D. Utilize carrier delay on all routers in the network.
Selected Answer: B
Question #: 63
Topic #: 1
How is a sub-second failure of a transport link detected in a Cisco SD-WAN network?
A. Hellos are sent between the WAN Edge routers and the vSmart controller.
B. BFD runs on the IPsec tunnels between WAN Edge routers.
C. BGP is used between WAN Edge routers and the vSmart controller.
D. Link state change messages are sent between vSmart controllers.
Selected Answer: B
Question #: 64
Topic #: 1
Refer to the exhibit. Which two solutions maximize the use of the links between the core and distribution layers? (Choose two.)
A. use multiple equal-cost links
B. use an IGP
C. use HSRP
D. use RPVSTP+
E. use multiple unequal-cost links
Selected Answer: AB
Question #: 65
Topic #: 1
A customer’s current Layer 2 infrastructure is running Spanning Tree 802.1d, and all configuration changes are manually implemented on each switch. An architect must redesign the Layer 2 domain to achieve these goals:
* reduce the impact of topology changes
* reduce the time spent on network administration
* reduce manual configuration errors
Which two solutions should the architect include in the new design? (Choose two.)
A. Implement Rapid PVST+ instead of STP.
B. Implement MST instead of STP.
C. Use VTP to propagate VLAN information and to prune unused VLANs.
D. Configure broadcast and multicast storm control on all switches.
E. Configure dynamic trunking protocol to propagate VLAN information.
Selected Answer: AC
Question #: 66
Topic #: 1
Which component is part of the Cisco SD-Access overlay architecture?
A. border node
B. spine node
C. leaf node
D. Cisco DNA Center
Selected Answer: A
Question #: 67
Topic #: 1
How are wireless endpoints registered in the HTDB in a Cisco SD-Access architecture?
A. Border nodes first register endpoints and then update the HTDB.
B. Fabric WLCs update the HTDB as new clients connect to the wireless network.
C. Fabric APs update the HTDB with the clients’ EID and RLOC.
D. Fabric edge nodes update the HTDB based on CAPPWAP messaging from the AP.
Selected Answer: D
Question #: 68
Topic #: 1
What is the purpose of a Cisco SD-Access underlay network?
A. to abstract IP-based connectivity from physical connectivity
B. to emulate LAN segments to transport Layer 2 frames over a Layer 3 network
C. to establish physical connectivity between switches and routers
D. to provide virtualization by encapsulating network traffic over IP tunnels
Selected Answer: C
Question #: 69
Topic #: 1
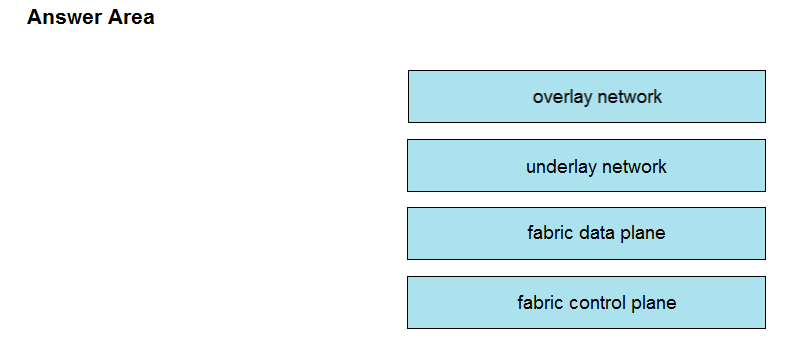
DRAG DROP –
Drag and drop the components in a Cisco SD-Access architecture from the left onto their descriptions on the right.
Select and Place:
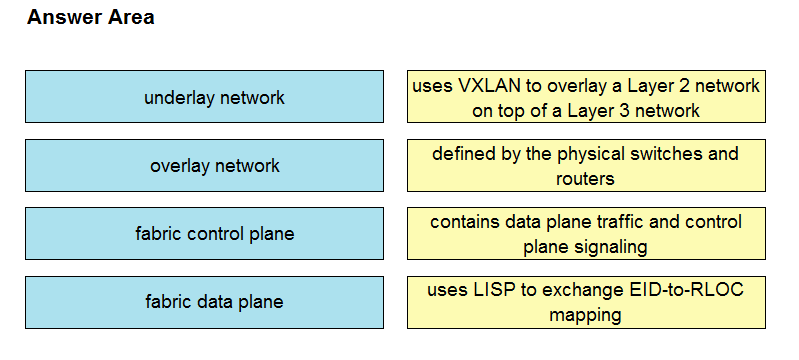
Suggestion Answer:
Question #: 70
Topic #: 1
Refer to the exhibit. The distribution switches serve as the Layer 3 boundary. HSRP preemption is enabled. When the primary switch comes back after a failure, traffic is initially dropped. Which solution must be implemented to improve the design?
A. Increase the hello timers on both HSRP devices.
B. Use the preempt delay feature on the backup HSRP device.
C. Use the preempt delay feature on the primary HSRP device.
D. Configure a higher mac-refresh interval on both HSRP devices.
Selected Answer: C
Question #: 71
Topic #: 1
Refer to the exhibit. Where must an architect plan for route summarization for the topology?
A. from the core toward the aggregation and the access toward the aggregation
B. from the core toward the aggregation and the aggregation toward the core
C. from the aggregation toward the access and the access toward the aggregation
D. from the aggregation toward the core and the aggregation toward the access
Selected Answer: D
Question #: 72
Topic #: 1
Refer to the exhibit. The connection between SW2 and SW3 is fiber and occasionally experiences unidirectional link failure. An architect must optimize the network to reduce the change of Layer 2 forwarding loops when the link fails. Which solution should the architect include?
A. Utilize BPDU filter on SW3.
B. Utilize root guard on SW1.
C. Utilize BPDU guard on SW1.
D. Utilize loop guard on SW2.
Selected Answer: D
Question #: 73
Topic #: 1
Refer to the exhibit. The full EIGRP routing table is advertised throughout the network. Currently, users experience data loss when any one link in the network fails. An architect must optimize the network to reduce the impact when a link fails. Which solution should the architect include in the design?
A. Run BFD on the inter links between EIGRP neighbors.
B. Summarize the access layer networks from each access layer switch toward the aggregation layer.
C. Reduce the default EIGRP hello interval and hold time.
D. Summarize the access layer networks from the aggregation layer toward the core layer.
Selected Answer: D
Question #: 74
Topic #: 1
What is the purpose of a control plane node in a Cisco SD-Access network fabric?
A. to maintain the endpoint database and mapping between endpoints and edge nodes
B. to detect endpoints in the fabric and inform the host tracking database of EID-to-fabric-edge node bindings
C. to identify and authenticate endpoints within the network fabric
D. to act as the network gateway between the network fabric and outside networks
Selected Answer: A
Question #: 75
Topic #: 1
Refer to the exhibit. An architect reviews the low-level design of a company’s enterprise network and advises optimizing the STP convergence time. Which functionality must be applied to Gi1/0/1-10 to follow the architect’s recommendation?
A. UplinkFast
B. root guard
C. BPDU guard
D. PortFast
Selected Answer: D
Question #: 76
Topic #: 1
An engineer must design a large Layer 2 domain that contains hundreds of switches and VLANs. The engineer’s primary goals are to:
✑ Efficiently utilize the bandwidth of all links
✑ Avoid Layer 2 loops
✑ Cause minimal impact on switch CPU and memory
Which technology should the engineer include in the design?
A. MST
B. Rapid PVST+
C. RSTP
D. PVST+
Selected Answer: A
Question #: 77
Topic #: 1
Refer to the exhibit. An engineer must design an automatic failover solution. The solution should allow HSRP to detect a WAN 1 failure and initiate an automatic failover, making router R2 the active HSRP router. Which two solutions should the engineer choose? (Choose two.)
A. implement IP SLA on router R1
B. implement PBR on router R1
C. implement Enhanced Object Tracking on router R1
D. use IP source routing
E. use a floating static route
Selected Answer: AC
Question #: 78
Topic #: 1
Which topology within a network underlay eliminates the need for first hop redundancy protocols while improving fault tolerance, increasing resiliency, and simplifying the network?
A. virtualized topology
B. routed access topology
C. Layer 2 topology
D. logical fabric topology
Selected Answer: B
Question #: 79
Topic #: 1
Refer to the exhibit.
A customer is running HSRP on the core routers. Over time the company has grown and requires more network capacity. In the current environment, some of the downstream interfaces are almost fully utilized, but others are not. Which solution improves the situation?
A. Make router R2 active for half of the VLANs.
B. Add more interfaces to R1 and R2.
C. Configure port channel toward downstream switches.
D. Enable RSTP on the downstream switches.
Selected Answer: A
Question #: 80
Topic #: 1
An architect must develop a campus network solution that includes:
✑ logically segmented and isolated networks
✑ ability to communicate between network segments when required
✑ support for overlapping IP addresses
✑ widely available technologies to avoid purchasing specialized equipment
Which solution must the architect select?
A. VSS with IGP
B. 802.1Q with HSRP
C. vPC with HSRP
D. VRF-Lite with OSPF
Selected Answer: D
Question #: 81
Topic #: 1
Which feature is used to optimize WAN bandwidth of IGMP network traffic among WAN Edge routers in the same VPN?
A. IGMPv2
B. multicast RP
C. multicast-replicator
D. multicast service routes
Selected Answer: C
Question #: 82
Topic #: 1
Which consideration must be made when designing a Cisco SD-Access fabric underlay?
A. Subnets must be reduced to decrease latency.
B. Up to six control planes are supported.
C. The default MTU should be increased.
D. A unified policy must be used.
Selected Answer: C
Question #: 83
Topic #: 1
Which two functions does the control plane node provide in a Cisco SD-Access architecture? (Choose two.)
A. LISP proxy ETR
B. host tracking database
C. policy mapping
D. map server
E. endpoint registration
Selected Answer: BD
Question #: 84
Topic #: 1
A large chain of stores currently uses MPLS-based T1 lines to connect their stores to their data center. An architect must design a new solution to improve availability and reduce costs while keeping these considerations in mind:
✑ The company uses multicast to deliver training to the stores.
✑ The company uses dynamic routing protocols and has implemented QoS.
✑ To simplify deployments, tunnels should be created dynamically on the hub when additional stores open.
Which solution should be included in this design?
A. VPLS
B. GET VPN
C. DMVPN
D. IPsec
Selected Answer: C
Question #: 85
Topic #: 1
A network engineer must connect two sites across a public network using a secure tunneling technology that supports multicast traffic. Which technology should be selected?
A. IPsec
B. GRE
C. PPTP
D. GRE over IPsec
Selected Answer: D
Question #: 86
Topic #: 1
A branch office has a primary L3VPN MPLS connection back to the main office and an IPSEC VPN tunnel that serves as backup. Which design ensures that data is sent over the backup connection only if the primary MPLS circuit is down?
A. Use EIGRP to establish a neighbor relationship with the main office via L3VPN MPLS and the IPSEC VPN tunnel.
B. Use BGP with the multipath feature enabled to force traffic via the primary path when available.
C. Use static routes tied to an IP SLA to prefer the primary path while a floating static route points to the backup connection.
D. Use OSPF with a passive-interface command on the backup connection.
Selected Answer: C
Question #: 87
Topic #: 1
Which solution allows overlay VNs to communicate with each other in an SD-WAN Architecture?
A. External fusion routers can be used to map VNs to VRFs and selectively route traffic between VRFs.
B. GRE tunneling can be configured between fabric edges to connect one VN to another.
C. SGTs can be used to permit traffic from one VN to another.
D. Route leaking can be used on the fabric border nodes to inject routes from one VN to another.
Selected Answer: D
Question #: 88
Topic #: 1
What are two benefits of designing an SD-WAN network fabric with direct Internet access implemented at every site? (Choose two.)
A. It decreases latency to applications hosted by public cloud service provider.
B. It decreases latency on Internet circuits.
C. It increases the speed of delivery of site deployments through zero-touch provisioning.
D. It increases the total available bandwidth on Internet circuits.
E. It alleviates network traffic on MPLS circuits.
Selected Answer: AE
Question #: 89
Topic #: 1
Which routes does the overlay management protocol advertise in an SD-WAN overlay?
A. underlay, MPLS, and overlay
B. primary, backup, and load-balanced
C. prefix, TLOC, and service
D. Internet, MPLS, and backup
Selected Answer: C
Question #: 90
Topic #: 1
What is one function of the vSmart controller in an SD-WAN deployment?
A. orchestrates vEdge and cEdge connectivity
B. responsible for the centralized control plane of the SD-WAN network
C. provides centralized network management and a GUI to monitor and operate the SD-WAN overlay
D. provides a data-plane at branch offices to pass traffic through the SD-WAN network
Selected Answer: B
Question #: 91
Topic #: 1
In an SD-WAN architecture, which methods are used to bootstrap a vEdge router?
A. DHCP options or manual configuration
B. vManage or DNS records
C. ZTP or manual configuration
D. DNS records or DHCP options
Selected Answer: C
Question #: 92
Topic #: 1
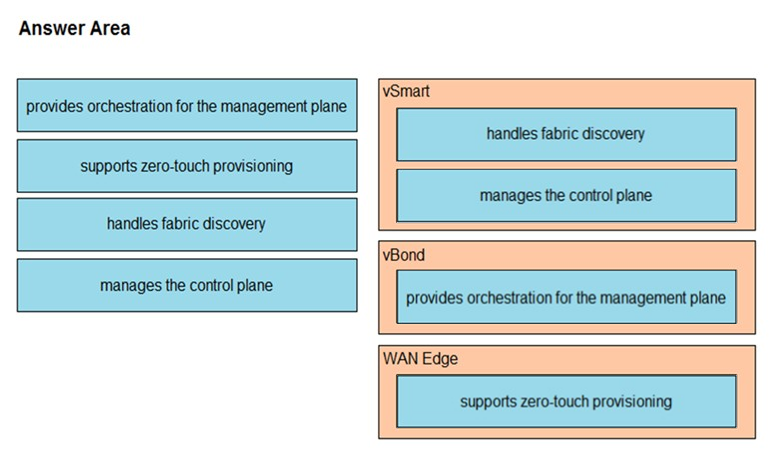
DRAG DROP –
Drag and drop the functions from the left onto the Cisco SD-WAN components that perform them on the right.
Select and Place:
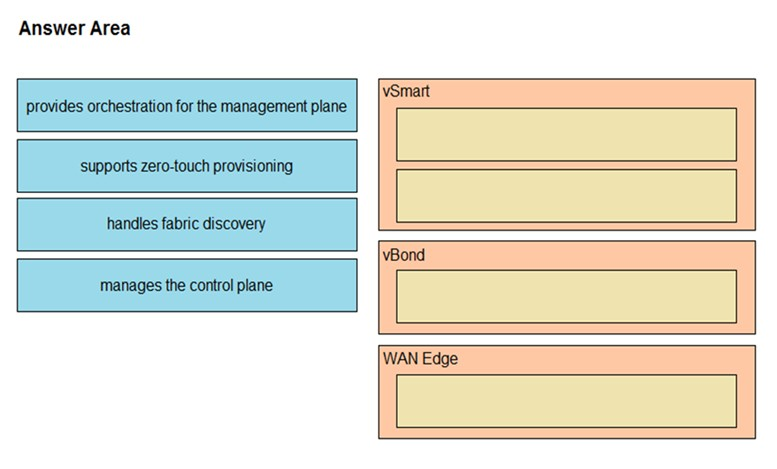
Suggestion Answer:
Question #: 93
Topic #: 1
Which two functions are provided by the Cisco SD-WAN orchestration plane? (Choose two.)
A. centralized provisioning
B. primary authentication point
C. NAT traversal facilitation
D. Zero Touch Provisioning
E. troubleshooting and monitoring
Selected Answer: BC
Question #: 94
Topic #: 1
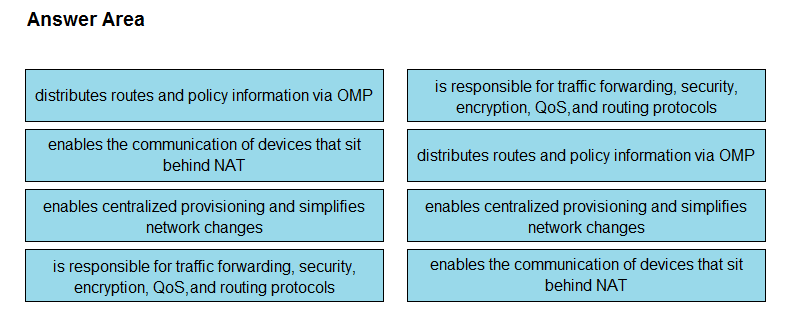
DRAG DROP –
Drag and drop the descriptions from the left onto the Cisco SD-WAN component they describe on the right.
Select and Place:
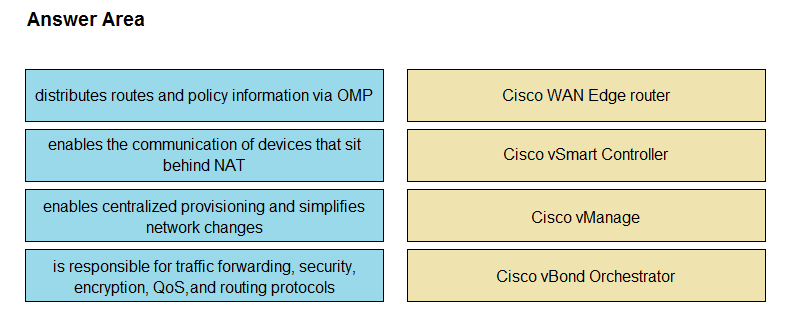
Suggestion Answer:
Question #: 95
Topic #: 1
Which two techniques improve the application experience in a Cisco SD-WAN design? (Choose two.)
A. utilizing forward error correction
B. implementing a stateful application firewall
C. implementing AMP
D. utilizing quality of service
E. implementing Cisco Umbrella
Selected Answer: AD
Question #: 96
Topic #: 1
How is redundancy achieved among Cisco vBond Orchestrators in a Cisco SD-WAN deployment?
A. The IP addresses of all Orchestrators are mapped to a single DNS name.
B. The closest Orchestrator to each Cisco WAN Edge router is selected.
C. Cisco WAN Edge routers are configured with all Orchestrators using their IP addresses and priority.
D. A single Cisco Orchestrator is deployed in each network.
Selected Answer: A
Question #: 97
Topic #: 1
Which design consideration must be made when dual WAN Edge routers are deployed at a branch site?
A. Use BGP AS-path prepending to influence egress traffic and use MED to influence ingress traffic from the branch.
B. HSRP priorities must match the OMP routing policy to prefer one WAN Edge over the other.
C. Traffic must be symmetrical as it egresses the WAN Edges and returns from remote sites for DPI to function properly.
D. Configure BFD between WAN Edge routers to detect sub-second link failures.
Selected Answer: C
Question #: 98
Topic #: 1
When IPsec VPNs are designed, what is a unique requirement if support for IP Multicast is required?
A. encapsulation of traffic with GRE or VTI
B. IPsec forwarding using transport mode
C. additional bandwidth for headend
D. IPsec forwarding using tunnel mode
Selected Answer: A
Question #: 99
Topic #: 1
Which control-plane technology allows the same subnet to exist across multiple network locations?
A. LISP
B. VXLAN
C. FabricPath
D. ISE mobility services
Selected Answer: B
Question #: 100
Topic #: 1
An engineer is upgrading a company’s main site to include a connection to a second ISP. The company will receive full Internet routing tables from both ISPs via
BGP. The engineer must ensure that the company does not become a transit autonomous system. Which solution should be included in this design?
A. Tag incoming routes from both ISPs with BGP community no-export.
B. Lower the MED for updates sent to the secondary ISP.
C. Use a route-map to prevent all prefixes from being advertised to either ISP.
D. Modify the local-preference for routes incoming from the primary ISP.
Selected Answer: A

